Updated for 2026 to reflect the latest account takeover fraud trends.
When it comes to cyber threat trends in 2026, risk will increasingly be defined less by new attack techniques and sophistication, and more by when defenses engage.
Across malware delivery, identity abuse, fraud, misinformation, and brand impersonation campaigns, the same pattern keeps emerging. Damage rarely occurs because controls are missing entirely. It occurs because protection activates after exploitation has already begun.
In short, attackers aren’t simply becoming more sophisticated. They’re operating on compressed timelines, shrinking the window between exposure and impact to a point where many defenses never meaningfully engage at all.
In this environment, timing has become the defining variable in cyber risk.
The Account Takeover Attack Window Is More Compressed than Ever
Over the past two years, the attack window has collapsed.
It’s no secret that automation has lowered the skill barrier required to launch effective deception-based account takeover (ATO) attacks, reduced preparation time, and shortened the gap between exposure and exploitation.
In many scenarios, attackers no longer require long-term persistence or deep access. All they need is brief moments of opportunity before detection logic activates.
In one specific case cited in the Social Engineering edition of Palo Alto Networks’ Unit 42 Global Incident Response Report, a threat actor (Muddled Libra) moved from initial access to Domain Administrator privileges in under 40 minutes. No sophisticated malware, no coding exploits – only “high-touch” social engineering.
A key aggravating factor is that most enterprise defenses remain optimized for investigation, confirmation, and response. These are essential capabilities, but they assume the organization will recognize risk in time to intervene.
With this in mind, here are Memcyco’s cyber threat projections for 2026.
Projection 1: Attackers Will Favor Attack Speed Over Sophistication Across Threat Types
The defining characteristic of many modern attacks in 2026 won’t be ingenuity and alone, but raw speed.
Automation allows attackers to test, launch, and discard campaigns faster than defenders can analyze them. According to the Social Engineering edition of Palo Alto Networks’ Unit 42 Global Incident Response Report, social engineering was the top initial access vector between May 2024 and May 2025 with 36% of all incidents in the IR caseload began with a social engineering tactic.
What’s notable is the report’s emphasis on scalability and repeatability of deception with ClickFix-like campaigns – rather than technically complex exploits – highlighting how attackers compromise accounts within about an hour of initial impersonation activity.
This pattern appears across threat classes:
- Scam and impersonation workflows optimize for rapid exposure rather than long-term stealth
- Malware campaigns increasingly prioritize fast initial access over complex payloads
- Disinformation and brand abuse succeed when false legitimacy spreads before verification
- Opportunistic cloud and SaaS exposure is exploited the moment it becomes visible
Across these scenarios, success depends less on technical complexity and more on whether exploitation occurs before controls engage.
Projection 2: ‘Trust Inheritance’ Will Emerge as a New Attack Surface
As digital ecosystems grow more interconnected, trust now propagates faster than validation mechanisms can reasonably keep pace.
Single sign-on, federated identity, third-party platforms, and embedded services all rely on inherited trust relationships. When those relationships are abused, attackers don’t need to compromise infrastructure directly. They exploit assumptions.
According to Crowdstrike’s 2025 Global Threat Report, 75% of initial access attempts in 2024/2025 were malware-free, relying instead on social engineering and identity misuse.
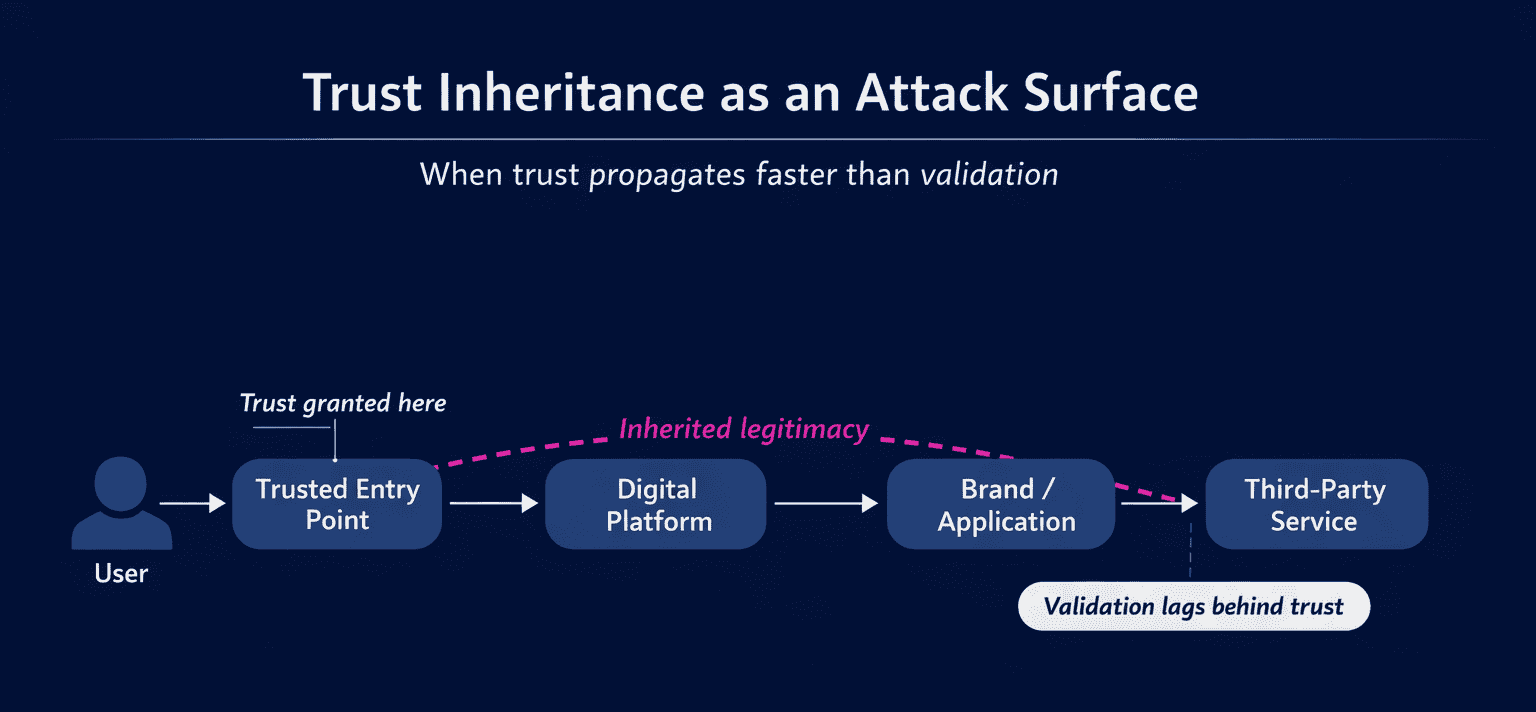
This shift changes the nature of exposure. Risk no longer sits only within owned systems. It moves through identity chains, brand associations, and user decisions that occur outside direct enterprise visibility.
The attack surface is no longer purely technical. It is relational. It increasingly reflects how trust is delegated between users, identity providers, platforms, and brands, rather than weaknesses in code or infrastructure.
Projection 3: Disruption and Misinformation Will Create Security Impact Without Breach
Not all security impact requires technical intrusion.
In 2026, many organizations will experience operational, reputational, or customer harm without a traditional breach ever occurring. Impersonation, misinformation, and false legitimacy signals can disrupt trust long before facts are corrected.
In 2024, Americans lost over $12.5 billion to fraud according to a March 2025 FTC press release, with brand impersonation and “false legitimacy” scams representing the fastest-growing categories.
By the time takedowns occur or statements are issued, the impact has already materialized. Customers have acted. Decisions have been made. Confidence has eroded.
Once again, timing determines outcome.
Domain takedowns are part of your brand protection toolkit, but standalone, it’s not strategy. Discover What Domain Takedown Services Miss & How to Close Gaps.
Projection 4: Initial Access Will Happen Earlier Than Most Security Controls Expect
Initial access no longer begins at the login prompt.
Search results, sponsored ads, social platforms, QR codes, shortened links, and mobile browser behaviors all create interception points upstream of authentication. Users are redirected, persuaded, or misled before enterprise security systems have context to evaluate risk.
This shift doesn’t bypass defenses directly. It renders them late. Incident response data reinforces this sequencing gap.
For example, Rapid7’s Q1 2025 Incident Response analysis found that valid credentials without Multifactor authentication (MFA) were involved in more than half of observed network intrusions, indicating that by the time security teams detect compromise, attackers are already operating inside trusted access paths.
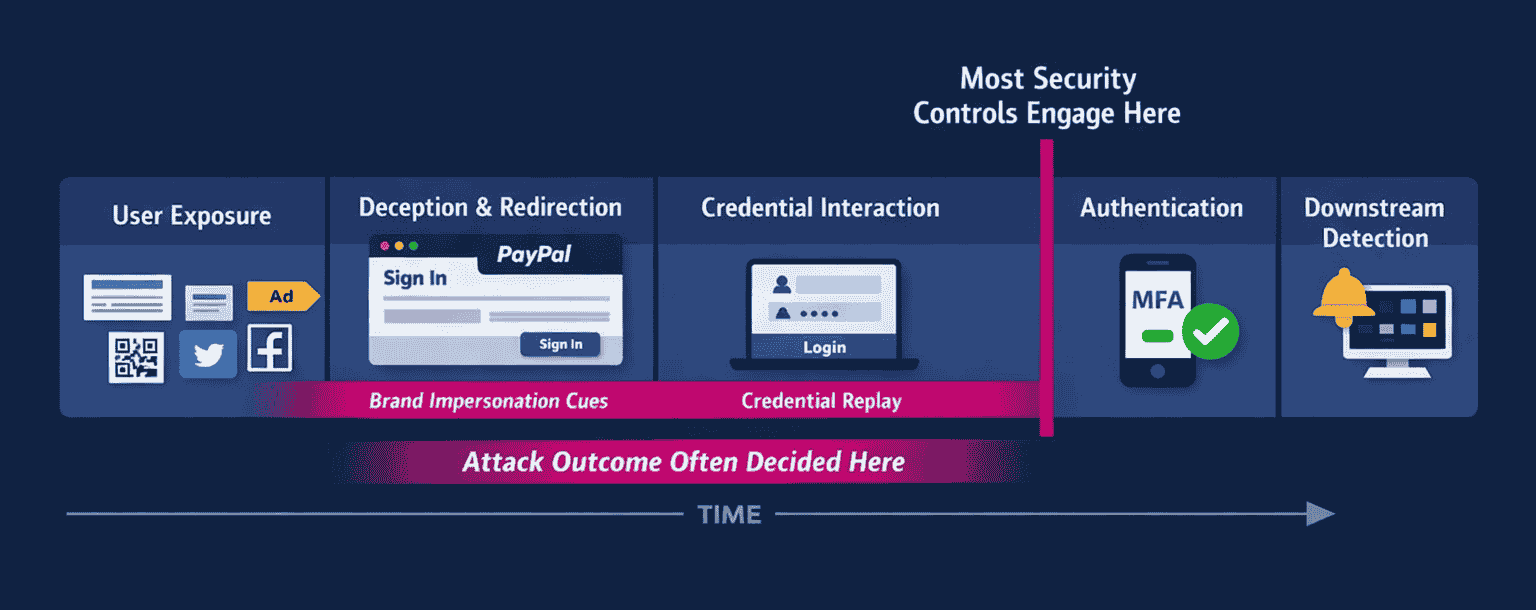
Account takeover makes this failure particularly visible, but the same pattern appears elsewhere. When interaction begins outside enterprise control, protection that activates only at authentication is already behind.
Learn how to extend your ATO threat visibility outside your enterprise perimiter, in our short guide: Account Takeover Detection in Action: The Telemetry Signals You’re Missing
Projection 5: Authentication Controls Will Remain Relevant, But Activate Chronically Late
Authentication remains a critical safeguard. MFA, step-up verification, and access policies aren’t broken.
What has changed is their position in the sequence.
Attackers increasingly influence the user journey before authentication decisions are evaluated. Credentials are harvested, sessions are relayed, or users are guided into flows that appear legitimate. By the time authentication controls evaluate risk, the attacker has already shaped the outcome.
According to Veriff’s 2026 Identity Fraud Report, 1 in 3 identity attacks in 2025 utilized AI-generated deepfakes or sophisticated session-hijacking tools to bypass MFA and traditional authentication.
This doesn’t mean MFA is obsolete. It wasn’t designed to act as the first line of defense against deception-driven attacks.
Learn more about how scammers bypass MFA, and how to reinforce it, in our guide:
How Attackers Bypass Authentication and What Actually Stops Account Takeovers.
Projection 6: Malware and Ransomware Will Be Outcomes of Earlier Failures
Malware and ransomware will continue to cause damage in 2026. But they’re increasingly not the starting point.
In many incidents, monetization occurs only after earlier failures: impersonation, credential theft, misdirected trust, or delayed detection. Focusing exclusively on payloads and endpoints treats the symptom, not the cause.
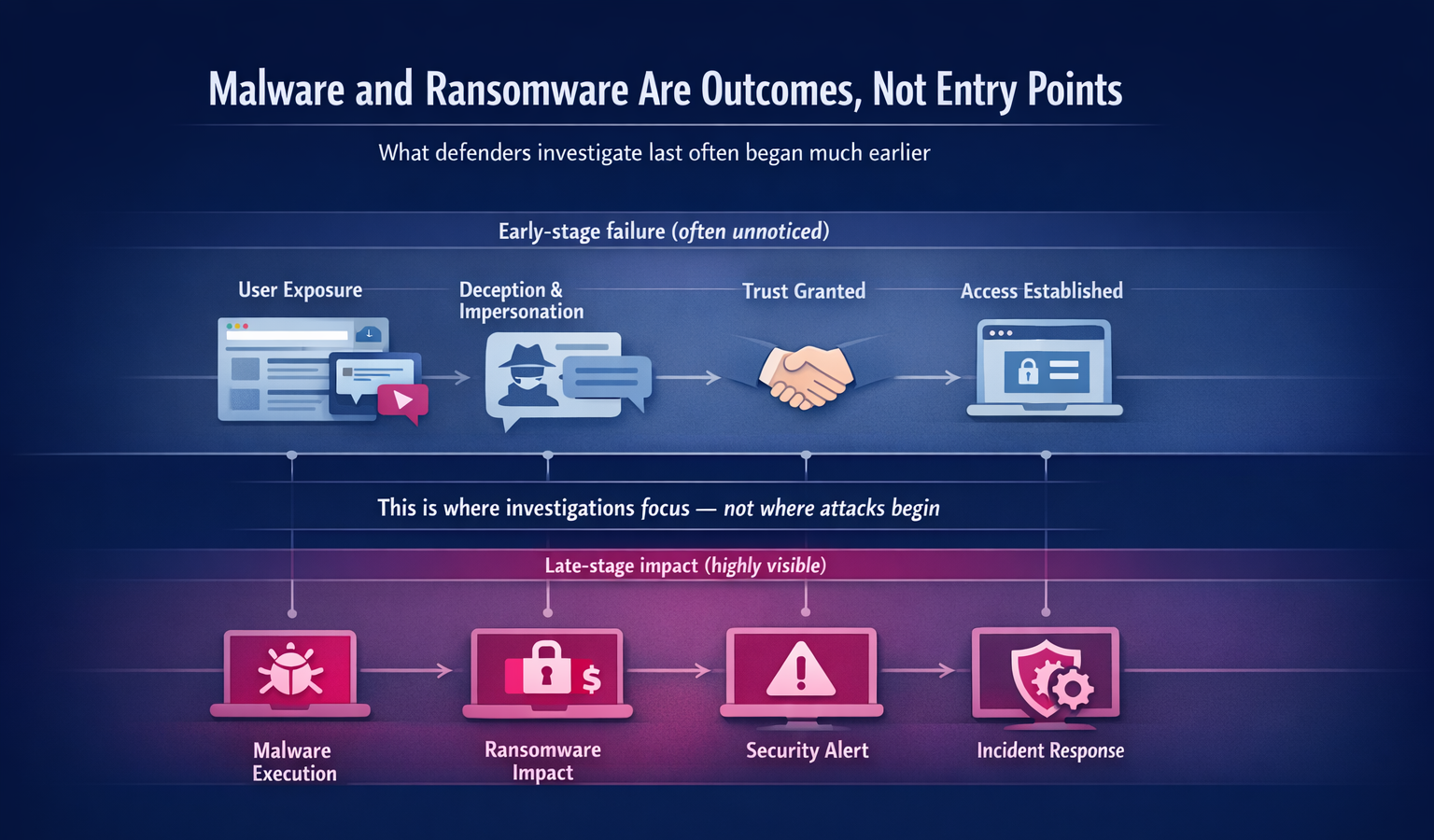
According to Verizon’s 2025 Data Breach Investigations Report shows ransomware present in 44% of analyzed breaches, marking a 37% increase from 2024. Yet initial access overwhelmingly stems from non-malware vectors like credential theft (often via phishing or impersonation) rather than direct payload delivery.
The bottom line is that, ultimately, the most effective prevention opportunities exist upstream, before malware becomes relevant.
The Pattern Across Vectors: Why Defenses Keep Missing the Moment of Exploitation
To sum up – across identity abuse, fraud, malware, misinformation, and brand impersonation, the same structural weakness appears.
Protection activates after exposure.
Detection logic is triggered once credentials are used, sessions are established, or damage is observable. By then, attackers have already succeeded in shaping user behavior or gaining leverage.
Different threats, same timing failure.
Why Account Takeover Makes the Timing Problem Impossible to Ignore
Account takeover exposes this pattern with particular clarity.
The sequence is visible. The financial and customer impact is immediate. Deception occurs upstream. Credentials are stolen or relayed. Authentication completes successfully. Only then does fraud become detectable.
Account takeover fraud makes this timing failure especially visible, because credentials are captured and replayed before traditional defenses engage.
ATO isn’t unique in this respect. It is simply the clearest illustration of what is happening elsewhere.
In 2026, Cyber Defense Success Will Be Decided by When those Defenses Engage
A preemptive cyber defense model shifts engagement earlier in the attack lifecycle, before technical compromise, account abuse, or transaction fraud becomes visible to downstream controls.
In many modern attacks, that early engagement point is deception, when users are redirected, impersonated, or misled before authentication or enforcement systems have sufficient context to intervene. This doesn’t redefine cyber defense as solely user-centric. It reflects where preemption most often begins.
Instead of waiting for authentication success or signals that a user is about to perform a sensitive account action, a preemptive approach engages during the moments when exploitation is initiated. It prioritizes early intent indicators over post-incident outcomes and focuses on preventing damage rather than investigating its aftermath.
This model doesn’t replace endpoint, network, or transaction controls. It changes when those controls are informed, ensuring they operate with earlier, higher-fidelity context rather than reacting after impact has already occurred.
Considering a switch to a preemptive cyber defense mode? Discover Why Fast Company Named Memcyco a 2025 ‘Next Big Thing in Tech’ for Cybersecurity
How Memcyco Addresses the Timing Gap in Account Takeover Scenarios
Memcyco’’s preemptive real-time platform engages at points in the attack sequence where traditional defenses typically activate too late. By operating during the login journey, Memcyco identifies impersonation and scam activity before stolen credentials are successfully reused or replayed, Identifying and protecting users at the moment of deception.
In short, Memcyco helps prevent account takeover from occurring in the first place. Rather than reacting to fraud after access is granted, Memcyco surfaces high-fidelity signals earlier in the authentication flow, allowing enterprises to both predict ATOs, and reduce their impact without adding friction for legitimate users.
In 2026, Cyber Defense Success Is Decided by When It Engages
The defining cyber risk of 2026 isn’t attacker sophistication. It is defensive timing.
As attack windows compress and trust moves faster than validation, protection that activates too late will continue to miss the moment that matters. Enterprises that shift engagement earlier will reduce damage across multiple threat classes, not just account takeover.
The future of cyber defense will belong to organizations that understand not just what to protect, but when protection must begin.
Book a product tour and discover why global enterprises choose Memcyco as part of their pivot to a preemptive model capable of effectively mitigating modern impersonation and ATO threats.
FAQs
1. Why don’t traditional security defenses stop modern cyber attacks?
Traditional security defenses often engage too late. They’re designed to investigate and respond after compromise indicators appear, while modern attacks exploit users and trust relationships earlier, shaping outcomes before controls have context to intervene.
2. Why isn’t multi-factor authentication enough to stop account takeover attacks?
Multi-factor authentication activates late in the attack sequence. Attackers increasingly manipulate users before authentication occurs, meaning MFA may validate access after credentials or user trust have already been compromised upstream.
3. What does trust inheritance mean in cybersecurity?
Trust inheritance describes risk created when digital systems extend legitimacy across identity providers, platforms, and partners faster than it can be verified. Attackers exploit these assumed trust relationships without breaching infrastructure or exploiting technical vulnerabilities.
4. Can a cyber attack cause damage without a data breach?
Yes. Cyber attacks can cause financial and reputational damage through brand impersonation, misinformation, and deception without breaching systems. In these cases, impact occurs through user decisions before enterprises detect any technical compromise.
5. What is preemptive cyber defense?
Preemptive cyber defense focuses on engaging earlier in the attack lifecycle, before authentication or transaction controls activate. It prioritizes detecting deception and high-risk intent signals to prevent exploitation rather than responding after damage occurs.



















